WordPress Security is one of the most important things to consider when you start using this CMS
WordPress is one of the most popular content management systems in the world. However, as with any popular platform, it's also a prime target for hackers.
That's why it's essential to follow WordPress security best practices to keep your website secure. In this comprehensive guide, we'll share practical tips and advice to help you improve your WordPress security.
In this article, I will guide you to one of the easiest steps to secure WordPress even for a beginner.
Best Practices for WordPress Security
1. Keep WordPress Updated
Keeping your WordPress site up to date is one of the simplest and most effective ways to improve your site's security. WordPress regularly releases updates and security patches to address vulnerabilities, and by keeping your site updated, you can reduce the risk of being hacked.
To update your WordPress site, simply log in to your Dashboard and click on the “Updates” tab. If there is a new version of WordPress available, you'll see a notification. Click on the “Update Now” button to install the latest version.
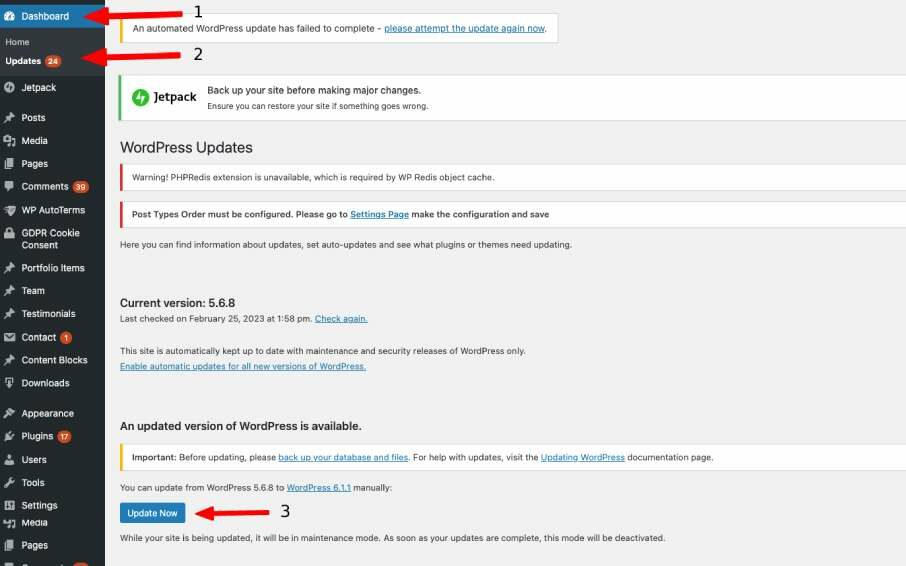
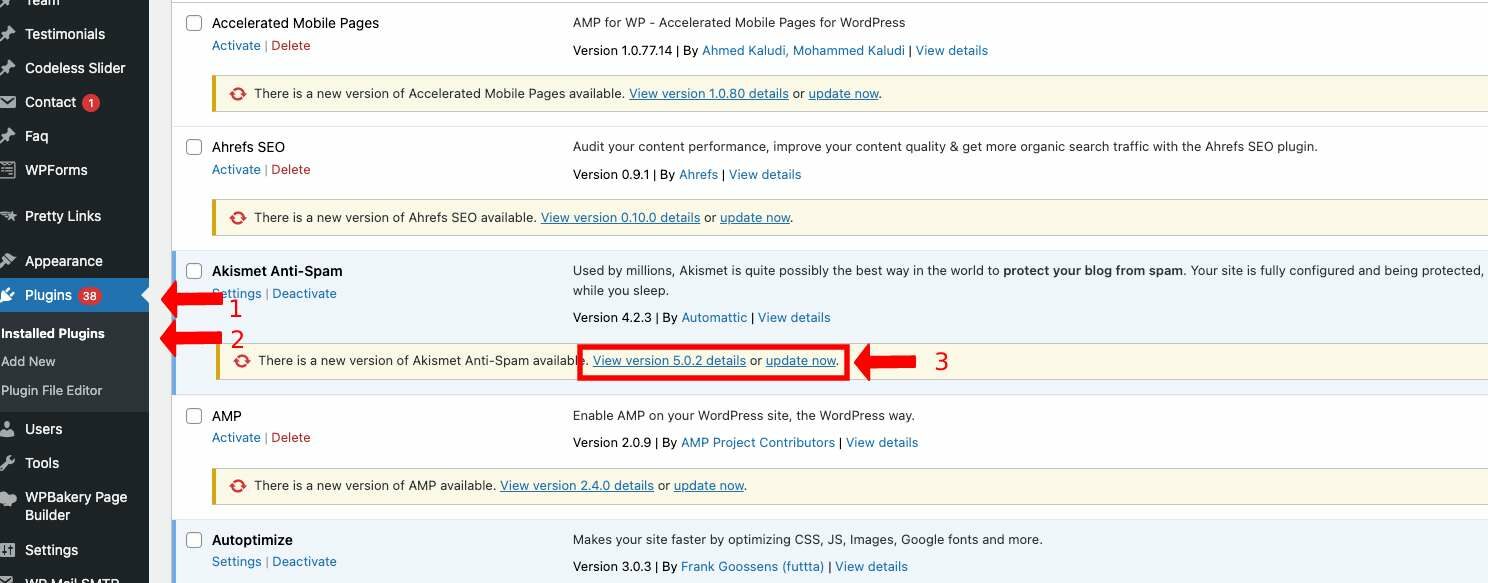
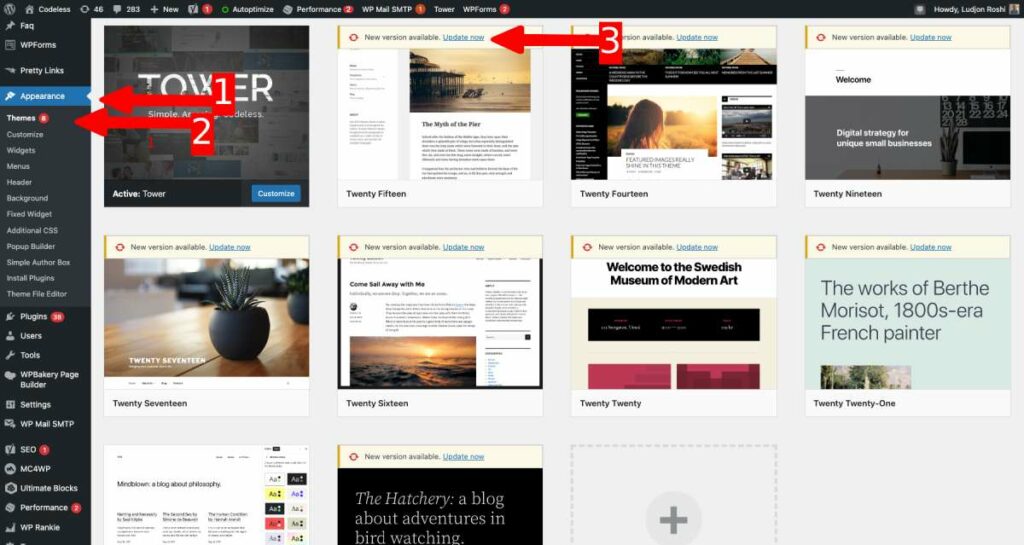
It's also essential to keep your themes and plugins updated. Themes and plugins can also have vulnerabilities that hackers can exploit, so it's crucial to keep them up to date. You can update your themes and plugins by going to the “Plugins” or “Appearance” tabs in your dashboard and clicking on the “Update” button.
2. Use Strong Passwords
Passwords are the first line of defense against hackers. Weak passwords can be easily guessed or cracked, making it easy for hackers to gain access to your site. To make your passwords strong, use a combination of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessable passwords like “password123” or “admin123.” These are some of the most commonly used passwords, and hackers can easily guess them. Instead, use a passphrase or a random combination of characters.
It's also a good idea to use a different password for every account you have. That way, if one password is compromised, your other accounts will still be secure.
3. Install a Security Plugin
Security plugins can help you protect your site from malware and other types of attacks. Some of the best security plugins for WordPress include Sucuri Security, Wordfence Security, and iThemes Security.
Security plugins can scan your site for vulnerabilities and help you address them. They can also monitor your site for suspicious activity and block malicious traffic. Some security plugins can even provide real-time alerts if your site is under attack.
When choosing a security plugin, make sure to read reviews and choose one that's regularly updated and actively maintained.
Here you can read a guide on how to configure Wordfence Security
4. Enable Two-Factor Authentication
Two-factor authentication adds an extra layer of security to your WordPress login process. With two-factor authentication, you'll need to enter a code sent to your phone or email in addition to your password. This helps prevent unauthorized access to your site.
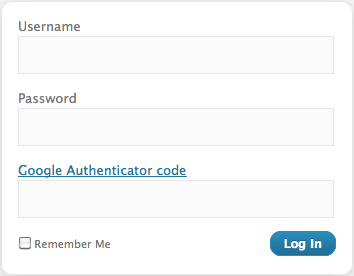
To enable two-factor authentication on your WordPress site, you can use a plugin like Google Authenticator. Google Authenticator generates a one-time code that you'll need to enter when logging in to your site.
5. Use HTTPS
HTTPS is a secure protocol that encrypts data transmitted between your site and your visitors' browsers. By using HTTPS, you can protect your visitors' sensitive information and improve your site's security.
To use HTTPS on your WordPress site, you'll need an SSL certificate. Many web hosts offer free SSL certificates through Let's Encrypt.
Once you have an SSL certificate installed, you can enable HTTPS by going to the “Settings” tab in your WordPress dashboard and changing the “WordPress Address” and “Site Address” URLs to “https://”.
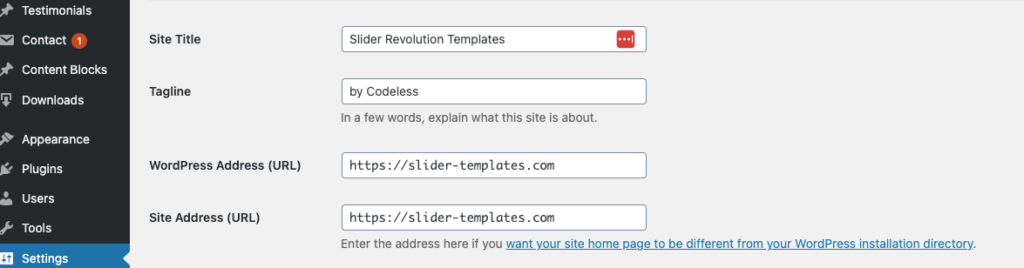
Here is a full tutorial on How to Easily add SSL and move WordPress from HTTP to HTTPS
6. Limit Login Attempts
Hackers often use brute force attacks to try and guess your login credentials. They use automated tools to try different combinations of usernames and passwords until they find the right one. To prevent brute force attacks, you can limit the number of login attempts allowed on your site.
You can use a plugin like Login LockDown or Jetpack to limit login attempts. These plugins will lock out a user after a certain number of failed login attempts. You can also set up a custom login URL to make it harder for hackers to find your login page.
7. Disable File Editing
WordPress allows you to edit your theme and plugin files directly from the dashboard. While this is convenient, it can also be a security risk. If a hacker gains access to your site, they can use the file editor to insert malicious code into your site's files.
To prevent this, you can disable the file editor by adding the following code to your wp-config.php file:
define('DISALLOW_FILE_EDIT', true);This will disable the file editor in your WordPress dashboard, making it harder for hackers to make changes to your site.
8. Use a Web Application Firewall
A web application firewall (WAF) is a security tool that filters traffic to your site and blocks malicious traffic. A WAF can help protect your site from attacks like SQL injection, cross-site scripting (XSS), and other types of attacks.
Some web hosts offer WAFs as part of their hosting package, but you can also use a third-party service like Cloudflare or Sucuri. These services can help improve your site's performance as well as its security.
9. Backup Your Site Regularly
Backing up your site regularly is one of the most important things you can do to protect your site. If your site is hacked or experiences a catastrophic failure, a backup can help you restore your site to its previous state.
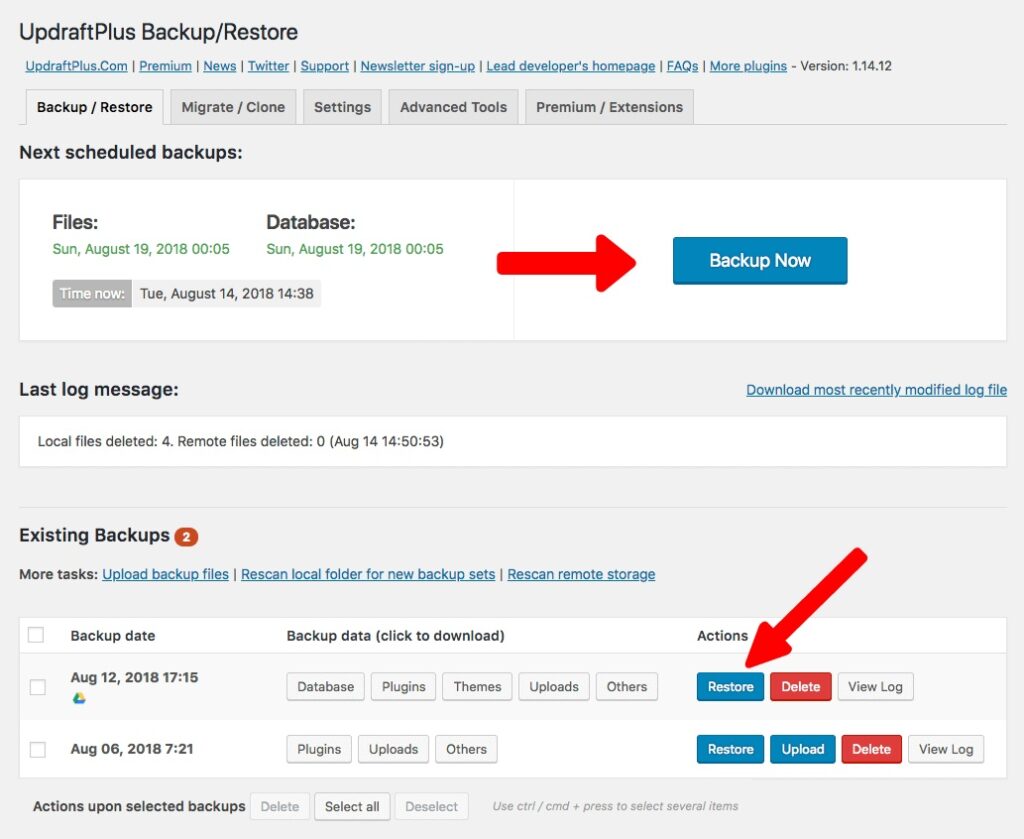
You can use a plugin like UpdraftPlus or Jetpack to schedule regular backups of your site. These plugins can store backups on remote servers like Dropbox or Google Drive, so you don't have to worry about losing your backups if your site is compromised.
10. Choose a Secure Web Host
Your web host plays a critical role in your site's security. If your web host has poor security practices, your site is at risk. When choosing a web host, look for one that takes security seriously.
Some things to look for in a secure web host include:
- Regular software updates and security patches
- Server-level security measures like firewalls and intrusion detection
- 24/7 security monitoring
- Automatic backups
- SSL certificate included
Read More: Best WordPress Hosting
Conclusion
In conclusion, WordPress security is a critical aspect of running a successful website. By following these best practices, you can improve your site's security and reduce the risk of being hacked.
Remember to keep your WordPress site and its plugins and themes updated, use strong passwords, install a security plugin, enable two-factor authentication, use HTTPS, limit login attempts, disable file editing, use a web application firewall, backup your site regularly, and choose a secure web host.
By implementing these best practices, you can rest assured that your site is well-protected against the latest threats and attacks. Stay vigilant and stay secure!
As one of the co-founders of Codeless, I bring to the table expertise in developing WordPress and web applications, as well as a track record of effectively managing hosting and servers. My passion for acquiring knowledge and my enthusiasm for constructing and testing novel technologies drive me to constantly innovate and improve.
Expertise:
Web Development,
Web Design,
Linux System Administration,
SEO
Experience:
15 years of experience in Web Development by developing and designing some of the most popular WordPress Themes like Specular, Tower, and Folie.
Education:
I have a degree in Engineering Physics and MSC in Material Science and Opto Electronics.






Comments
Hey there Roshi,
I was thinking, how do hackers redirect visitors from a website? For some days, my website is losing organic traffic.
Hi Adrita, they add custom codes to your files to make the redirection to another website. I suggest you to add and run the WordFence plugin. It can help with modified files.