The security of website applications is more important as the internet takes a center role in modern business operations. Cyber threats keep evolving, making it necessary for organizations to prioritize security measures.
Web applications are gateways to sensitive data, making them a target for malicious persons. The cybersecurity sector keeps changing, with new attack vectors and vulnerabilities emerging. Adopting a proactive and comprehensive approach to security is very important.
You can also read more: WordPress Security Guide For Beginners 2025
Understanding Web Application Threats
Knowing the nature of the threat landscape is important for securing web applications. Threats include various types of vulnerabilities that can compromise the integrity and security of these apps.
Recognizing these threats allows organizations to implement appropriate security measures and mitigate risks. Below are the most common threats facing web apps:
Injection Attacks
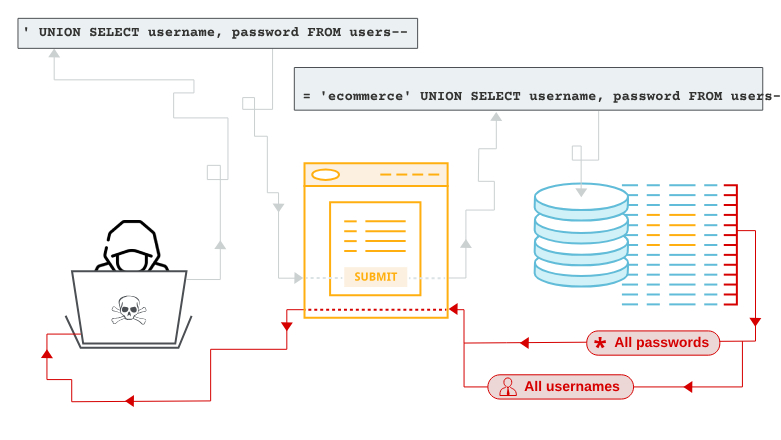
They are the most prevalent and dangerous threats. They occur when untrusted links or data are sent as part of a query or command. SQL is the most common injection attack that occurs when malicious SQL queries are used to manipulate a database. Attackers can also use cross-site scripting or command injection to exploit vulnerable applications.
Authentication and Session Management Vulnerabilities

Weak authentication and poor session management also expose web apps to threats. The three key vulnerabilities that exist here are:
- Weak passwords: Hackers can easily track simple or reused passwords. This gives them unlimited unauthorized access.
- Session hijacking: Malicious persons can also impersonate legitimate users by stealing or forging session cookies.
- Insecure token generation: Attackers can compromise easily predictable session tokens, giving them access to sensitive information.
Security Misconfiguration
This primarily occurs when security settings are not configured properly or left at default. Using default credentials like usernames and passwords on web apps makes them easier targets. Similarly, enabling unnecessary features can compromise web application security. Hackers can exploit features like debug models when needed.
Sensitive Data Exposure

This occurs when web applications mistakenly expose sensitive information like personal, authentication, or credit card details. Though rare, this can occur due to insecure data transmission or improper storage. Hackers can intercept data transmission if sent over networks without HTTPS configuration. Similarly, storing these details in plain text or using weak encryption methods can lead to breaches.
Third-party component risks
Most web applications rely on third-party components, especially libraries and frameworks. Organizations prefer to expedite development, enhance functionality, and reduce costs. While they are beneficial, they introduce significant security risks if not handled properly. Some third-party components contain vulnerabilities that malicious persons can exploit. These issues often stem from coding errors or outdated dependencies.
That aside, most third-party components are maintained by open-source communities or external developers. They may not be regularly updated, leaving web apps exposed to basic vulnerabilities.
Best Practices for Securing Web Applications
1. Adopting Strong Authentication Mechanisms

Introducing strong authentication mechanisms is key to ensuring the security of web applications. Authentication helps verify user identity before accessing sensitive functionalities or data in the application. Weak mechanisms can lead to unauthorized access and data breaches.
Businesses can improve their authentication mechanisms in many ways. First is through password policies and hashing. Implementing strong password policies helps thwart brute-force attacks and attempts of password guessing. Passwords should be complicated, with combined uppercase and lowercase letters, special characters, and numbers. They should also be hashed before being stored.
The second authentication mechanism is session management. Doing this prevents hijacking and unauthorized access to verified user accounts. This essentially involves having session timeouts, where active sessions expire automatically after some period of inactivity.
Adopting multi–factor authentication is the third and most effective authentication measure. This additional security layer requires users to satisfy multiple verification options before accessing their accounts. This may be a combination of passwords and biometrics. These options reduce the risks of unauthorized access.
2. Keep Software and Libraries Updated

Organizations should also keep their software and libraries updated to maintain the security and integrity of their website applications. Technological advances mean software vendors and open-source communities release new updates and patches to malicious code with known vulnerabilities. Not updating your software components on time leaves your web applications vulnerable to exploitation.
Organizations should begin by automating software update mechanisms. Implementing automated updates streamlines the processes of applying patches and security updates. Organizations should use tools like package managers to automate the detection, downloading, and installation of available updates. This reduces the burden on IT teams.
Organizations should have a robust patch management process that ensures timely updates to their application stacks. This includes application frameworks, web servers, and third-party libraries. They should also monitor vendor advisories regularly and vulnerability databases to stay informed of the latest patches and updates that suit their tech stack.
Conducting regular vulnerability scans and assessments is also important. It helps businesses identify outdated or vulnerable components in their application stack. Fortunately, automated scanning tools, like static code analysis tools, can help detect vulnerabilities present in software libraries.
Similarly, they should be tested in a controlled environment before integrating updates to applications. This allows organizations to evaluate the impact of these updates on the performance and functionality of their web applications before deploying them fully. Testing helps mitigate the risk of unintended consequences brought by updates.
Lastly, software updates can occasionally introduce unexpected issues even with careful testing. Organizations should establish rollback procedures and contingency plans. This helps them revert to their initial stable state in case of failed updates or unexpected behavior. Having rollback procedures minimizes downtime in case of unexpected emergencies.
3. Conduct Regular Assessment and Penetration Tests

Regular assessments are a proactive approach to identifying and addressing vulnerabilities in web applications. These assessments help evaluate the security status of web applications. Penetration tests involve creating a simulated real-world attack on the app.
Ethical hackers use various techniques to identify possible entry points attackers may use. Red teaming simulates the different attack scenarios to help organizations gain insights into their general security posture and prioritize remediation of identified vulnerabilities. The importance of conducting such assessments includes:
- Identifying vulnerabilities: These assessments typically start by identifying potential vulnerabilities in the app. A combination of automated scanning tools and manual code reviews may be used. Automated scanners detect common vulnerabilities like injection flaws, while manual code reviews are done by experienced professionals.
- Risk prioritization: Not all threats have the same level of risk. Security assessments help prioritize risks. Organizations can identify and focus on mitigating vulnerabilities with the greatest threat to system integrity.
- Reporting and remediation: Organizations should compile a detailed report after the security assessment. The report should highlight the identified vulnerabilities, if any, severity levels, and effective remediation procedures.
Remember that web app security should be an ongoing process. Organizations should regularly assess and test their systems. This ensures they adapt to continually evolving threats and vulnerabilities. Establishing a culture of continuous improvement, which includes security assessment, is prudent. It helps organizations maintain and enhance their security posture. They can minimize the risks of security breaches or prepare better for emerging threats.
4. Implement Security Headers and Content Security Policy

Security headers and content security policies are reliable security measures for web applications. These options provide additional defense against common vulnerabilities. To begin with, security headers are essentially HTTP response headers used by web applications to instruct browsers on how to behave in specific situations.
By doing this, they enforce rules on data transmission and content handling, helping mitigate various forms of attacks. For instance, HTTP ensures that browsers only interact with websites over HTTPS. This prevents cookie hijacking and downgrade attacks.
Similarly, a content security policy is a solid security strategy that prevents a diverse range of attacks. It specifies content sources that are allowed to be loaded and executed by browsers. This mitigates attacks like cross-site scripting and data injection.
5. Sanitize and Validate Input Data

Sanitizing and validating input data also helps secure web apps against injection attacks and other forms of threats. Validating inputs ensures that data entered into the system conforms to the expected formats. On the other hand, sanitization removes dangerous inputs to neutralize threats. Maintaining this dual approach helps maintain data integrity. Some of the benefits and best practices of sanitizing and validating input data include:
- Prevents injection attacks: Inject attacks like SQL exploit vulnerabilities by sending malicious links or data through input fields. Proper validation prevents attackers from injecting damaging codes. It ensures that input data doesn’t contain suspicious characters.
- Maintains data integrity: Validation also ensures that input data adheres to expected formats and ranges. This is vital in maintaining data integrity and prevents abnormal behavior in applications.
- Enhance security and user experience: Validation and sanitization improve security as it ensures that only correctly formatted data is processed by web applications.
Organizations should observe various best practices for input validation and sanitization. For instance, organizations should clearly define the constraints for each field. These are the allowed characters, format, and type. Enforcing these constraints on the client and server-side ensures that only valid data is entered.
Conclusion
Securing web applications requires a proactive approach and a thorough understanding of the changing threat landscape. Implementing robust cybersecurity measures like input validation and reliable authentication mechanisms can significantly mitigate these risks. Besides, staying informed and updated on emerging threats is important for maintaining the integrity of web apps in the current interconnected digital ecosystem.
As one of the co-founders of Codeless, I bring to the table expertise in developing WordPress and web applications, as well as a track record of effectively managing hosting and servers. My passion for acquiring knowledge and my enthusiasm for constructing and testing novel technologies drive me to constantly innovate and improve.
Expertise:
Web Development,
Web Design,
Linux System Administration,
SEO
Experience:
15 years of experience in Web Development by developing and designing some of the most popular WordPress Themes like Specular, Tower, and Folie.
Education:
I have a degree in Engineering Physics and MSC in Material Science and Opto Electronics.







Comments