A Virtual Private Server (VPS) provides a virtualized computing environment, offering the power and control of a dedicated server at a fraction of the cost. VPS hosting is a popular choice for businesses and developers who need more flexibility and resources than shared hosting can provide. However, with this increased power comes the critical responsibility of securing the server against potential threats.
Securing a VPS is crucial because it is often targeted by cybercriminals seeking to exploit vulnerabilities for data theft, malware distribution, or server hijacking. Common security threats include brute force attacks, malware infections, unauthorized access, and denial-of-service (DoS) attacks. These threats can lead to data breaches, service disruptions, and significant financial losses.
Understanding and implementing robust security measures is essential to protect your VPS. This guide will provide practical advice on minimizing attack surface, configuring strong authentication mechanisms, managing firewalls, and more. By following these best practices, you can significantly enhance the security of your VPS and safeguard your data and applications from malicious activities.
Best Practices for Securing Your VPS
Securing your VPS involves implementing a series of best practices designed to protect your server from potential threats. Here are some essential steps to ensure your VPS remains secure:
Regular Updates and Patch Management
- Importance of Updates: Keeping your software up-to-date is one of the simplest yet most effective ways to secure your VPS. Updates often include patches for security vulnerabilities that attackers could exploit.
- Automated vs. Manual Updates: Consider enabling automated updates for critical security patches. A manual approach may be preferred for other updates to ensure compatibility and stability.
Strong Authentication Mechanisms
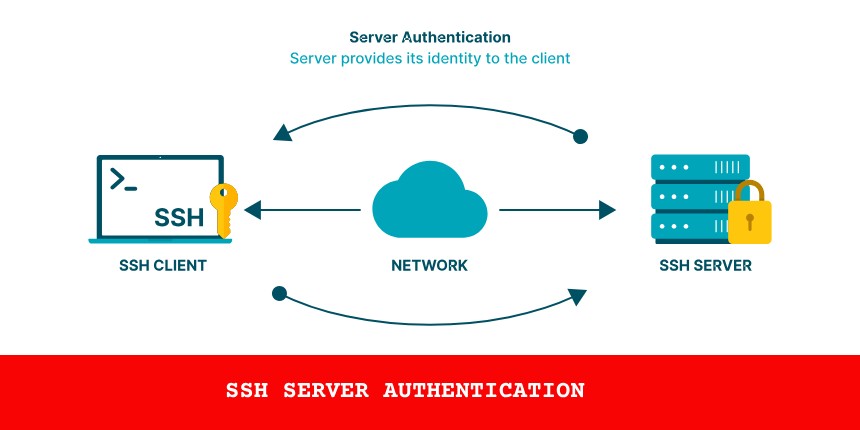
- SSH Keys: Use SSH keys instead of passwords for accessing your VPS. SSH keys provide a higher level of security because they are not susceptible to brute force attacks.
- Two-Factor Authentication (2FA): Implement 2FA to add an extra layer of security. Even if your password is compromised, 2FA can prevent unauthorized access.
Firewall Configuration
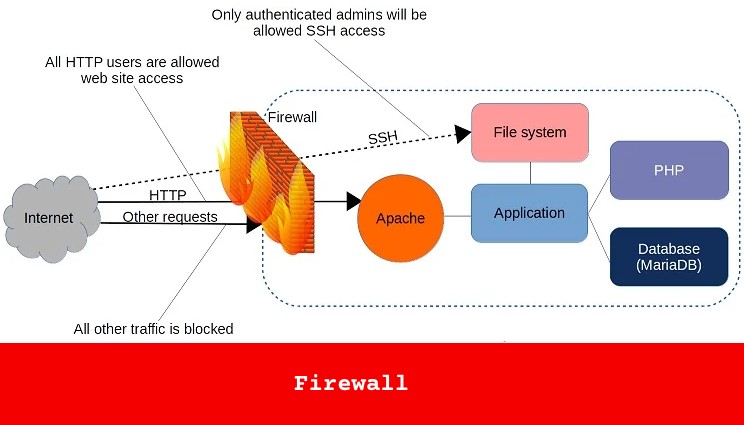
- Setting Up a Firewall: A firewall is your first line of defense against unauthorized access. Configure your firewall to allow only the necessary traffic to and from your VPS. (You can use Linux iptables or ufw – Uncomplicated Firewall)
- Common Firewall Rules: Implement rules to block all incoming traffic by default and only allow specific ports and IP addresses needed for your applications.
Intrusion Detection Systems (IDS)
- Types of IDS: Network-based IDS monitor network traffic for suspicious activity, while host-based IDS focus on monitoring the system itself.
- Implementation and Monitoring: Deploy an IDS to monitor your VPS for signs of intrusion continuously. Regularly review IDS alerts and logs to respond promptly to potential threats.
Data Protection and Backup Strategies
Protecting your data and ensuring you can recover from any incident are critical aspects of VPS security. Here are some strategies to help safeguard your data:
Encryption
- Importance of Encryption: Encrypting data both at rest and in transit is essential to protect sensitive information from unauthorized access. Encryption ensures that even if data is intercepted or accessed without permission, it remains unreadable.
- Tools and Methods:
- Data at Rest: Use full-disk encryption tools like LUKS (Linux Unified Key Setup) to encrypt the entire storage device. For databases, consider using built-in encryption features provided by the database management system.
- Data in Transit: Implement SSL/TLS certificates to encrypt data transmitted over networks. Tools like Let's Encrypt provide free SSL/TLS certificates for securing web traffic.
Regular Backups
- Scheduling Backups: Establish a regular backup schedule to ensure that all critical data is backed up frequently. Depending on the nature of your data, you might choose daily, weekly, or even real-time backups.
- Backup Strategies:
- Full Backups: Periodically perform full backups of your entire system, which capture all data and configurations.
- Incremental Backups: Use incremental backups to save only the changes made since the last backup. This approach reduces storage requirements and speeds up the backup process.
- Differential Backups: Similar to incremental backups, differential backups save changes made since the last full backup, providing a balance between speed and data recovery complexity.
- Storing Backups Securely: Store backups in a secure, off-site location to protect against data loss due to physical damage, theft, or other local incidents. Consider using cloud-based backup services for redundancy and ease of access.
Monitoring and Logging
Effective monitoring and logging are crucial for identifying and responding to security incidents promptly.
System Monitoring Tools
- Examples of Monitoring Tools: Use tools like Nagios, Zabbix, or Prometheus to monitor your VPS's performance and security. These tools can track various metrics, such as CPU usage, memory utilization, and network traffic.
- Setting Up Alerts: Configure alerts to notify you of any unusual or suspicious activity. This could include login attempts from unfamiliar IP addresses, sudden spikes in resource usage, or unauthorized changes to system files.
Log Management
- Importance of Maintaining Logs: Logs provide a record of system activity that can be invaluable for diagnosing issues and investigating security incidents. Ensure that logging is enabled for all critical services and applications.
- Tools for Log Management: Use tools like the ELK Stack (Elasticsearch, Logstash, Kibana) to collect, analyze, and visualize logs. Regularly review logs to identify any anomalies or signs of compromise.
- Log Retention Policies: Implement log retention policies to keep logs for an appropriate duration, balancing the need for historical data with storage constraints. Ensure that logs are stored securely and protected from unauthorized access.
By following these data protection and backup strategies, you can enhance the resilience of your VPS, ensuring that your data remains secure and recoverable in the event of a security breach or other incidents.
User Management and Access Control
Proper user management and access control are vital components of VPS security. Ensuring that only authorized users have access and that their permissions are correctly managed can significantly reduce the risk of unauthorized access and data breaches.
Principle of Least Privilege
- Minimal Permissions: Assign users the minimum level of access required to perform their tasks. This reduces the potential damage from compromised accounts.
- Regular Permission Reviews: Periodically review user permissions to ensure they are still appropriate. Remove or update permissions for users who no longer need them.
Secure Access Policies
- Strong Password Policies: Enforce strong password policies requiring complex and unique passwords. Encourage or mandate the use of password managers to help users manage their passwords securely.
- Account Lockout Policies: Implement account lockout policies to prevent brute force attacks. After a certain number of failed login attempts, lock the account and notify the user or an administrator.
- Session Timeouts: Configure session timeouts to log out users after a period of inactivity. This helps prevent unauthorized access from unattended sessions.
Multi-Factor Authentication (MFA)
- Implement MFA: Add an extra layer of security by requiring users to provide two or more verification factors to access their accounts. This can include something they know (password), something they have (security token), or something they are (biometric verification).
- MFA Tools: Use MFA tools and services such as Google Authenticator, Authy, or hardware tokens like YubiKey.
Access Control Lists (ACLs)
- Granular Access Control: Use ACLs to define which users or system processes can access specific resources. This allows for fine-tuned control over user permissions.
- File and Directory Permissions: Carefully configure file and directory permissions to ensure that sensitive data is only accessible to authorized users. Use tools like
chmod,chown, andsetfaclto manage these permissions.
User Account Management
- Create Separate User Accounts: Avoid using the root account for daily operations. Create separate user accounts with appropriate privileges for different tasks.
- Disable Unused Accounts: Regularly audit user accounts and disable or remove accounts that are no longer needed. This reduces the number of potential entry points for attackers.
- Use of Sudo: Configure sudo to allow users to perform administrative tasks without needing full root access. This can be managed through the
/etc/sudoersfile.
Secure Remote Access
- VPN for Remote Access: Require users to connect through a Virtual Private Network (VPN) when accessing the VPS remotely. This encrypts the connection and adds an extra layer of security.
- SSH Configuration:
- Disable Root Login: Prevent direct root login by setting
PermitRootLogin noin the SSH configuration file (/etc/ssh/sshd_config). - Change Default SSH Port: Change the default SSH port (22) to a non-standard port to reduce the risk of automated attacks.
- SSH Key Authentication: Require SSH key authentication instead of passwords for accessing the VPS. Ensure that keys are protected with strong passphrases.
- Disable Root Login: Prevent direct root login by setting
By implementing robust user management and access control measures, you can significantly enhance the security of your VPS, ensuring that only authorized users have access and that their activities are properly monitored and controlled.
Conclusion
Securing your VPS is an ongoing process that requires attention to detail and a proactive approach. By implementing the best practices outlined in this guide, you can protect your server from a wide range of security threats and ensure that your data and applications remain safe.
As one of the co-founders of Codeless, I bring to the table expertise in developing WordPress and web applications, as well as a track record of effectively managing hosting and servers. My passion for acquiring knowledge and my enthusiasm for constructing and testing novel technologies drive me to constantly innovate and improve.
Expertise:
Web Development,
Web Design,
Linux System Administration,
SEO
Experience:
15 years of experience in Web Development by developing and designing some of the most popular WordPress Themes like Specular, Tower, and Folie.
Education:
I have a degree in Engineering Physics and MSC in Material Science and Opto Electronics.







Comments